what is clean code?
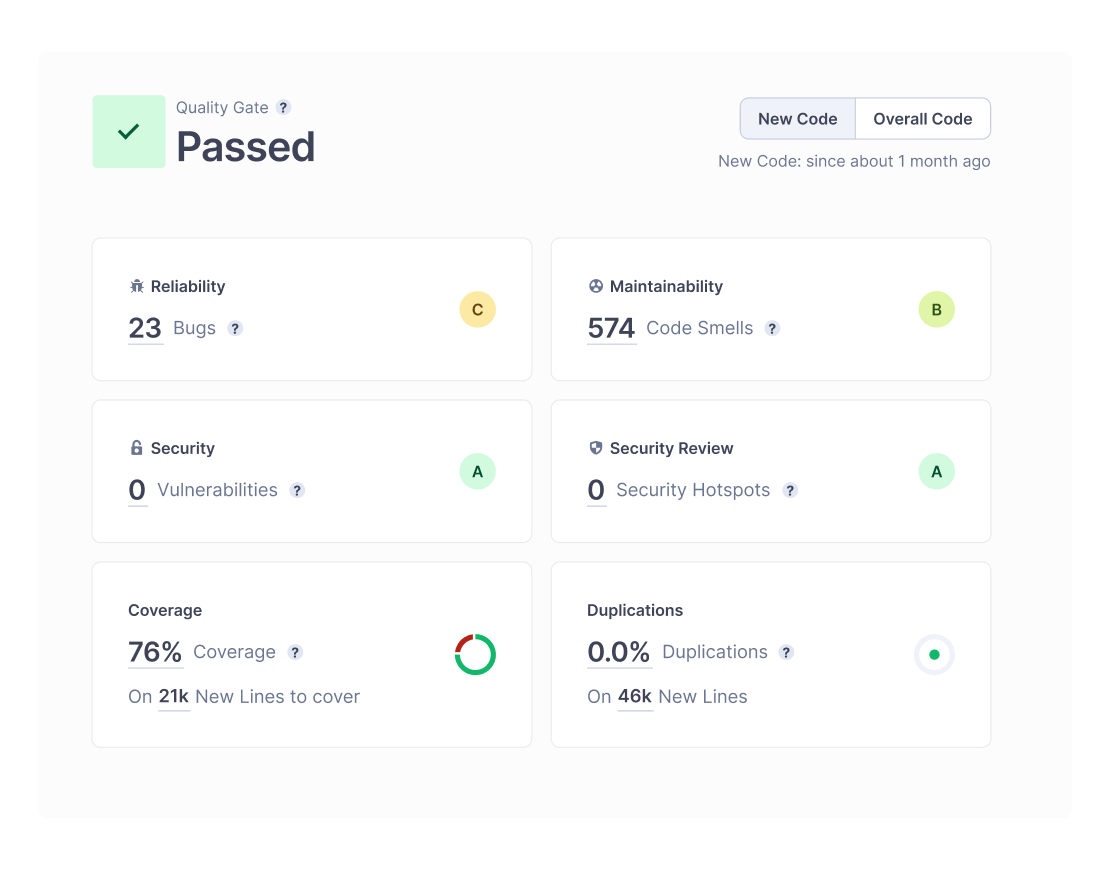
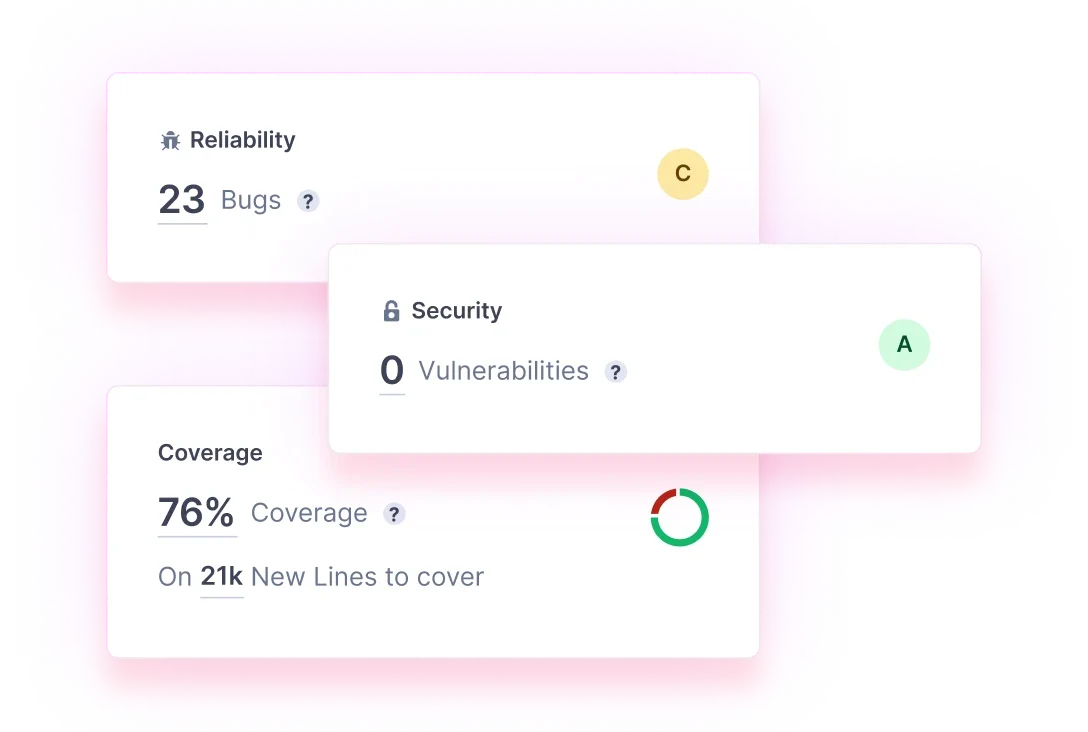
Clean Code is code that’s easily understandable, portable, and capable to change through structure and consistency but remains maintainable, reliable, and secure for performance demands.
Clean Code is well-documented coding standards that are clear and concise for increasing developer collaboration and communication.